Architecture
Prividium™ is built on a permissioned Validium chain with integrated, role-based access control. It runs a private instance of the ZKsync Chain, complete with its own sequencer and prover, inside an organization’s infrastructure or cloud. All transaction data and state are stored off-chain in a secure database, ensuring privacy by design.
A Proxy RPC layer serves as the single entry point to the network. All interactions — from users, enterprise applications, block explorers, or bridge operations — must pass through this proxy. It enforces fine-grained access rules using the Prividium™ Permissioning System, ensuring that only authenticated and authorized requests reach the chain. By separating the public interface from internal blockchain components, Prividium™ prevents unauthorized access and safeguards sensitive data.
State updates are finalized on Ethereum through the ZKsync Gateway, which receives the chain’s state roots and zero-knowledge proofs. This anchors the chain to Ethereum, providing L1-grade security and enabling interoperability with other ZKsync Chains.
This architecture delivers privacy, compliance, and auditability at the L2 level while inheriting the trust and finality of Ethereum, making Prividium™ ideal for institutional use cases such as trading, settlement, asset issuance, and compliance-sensitive workflows.
Figure: High-level architecture of Prividium™.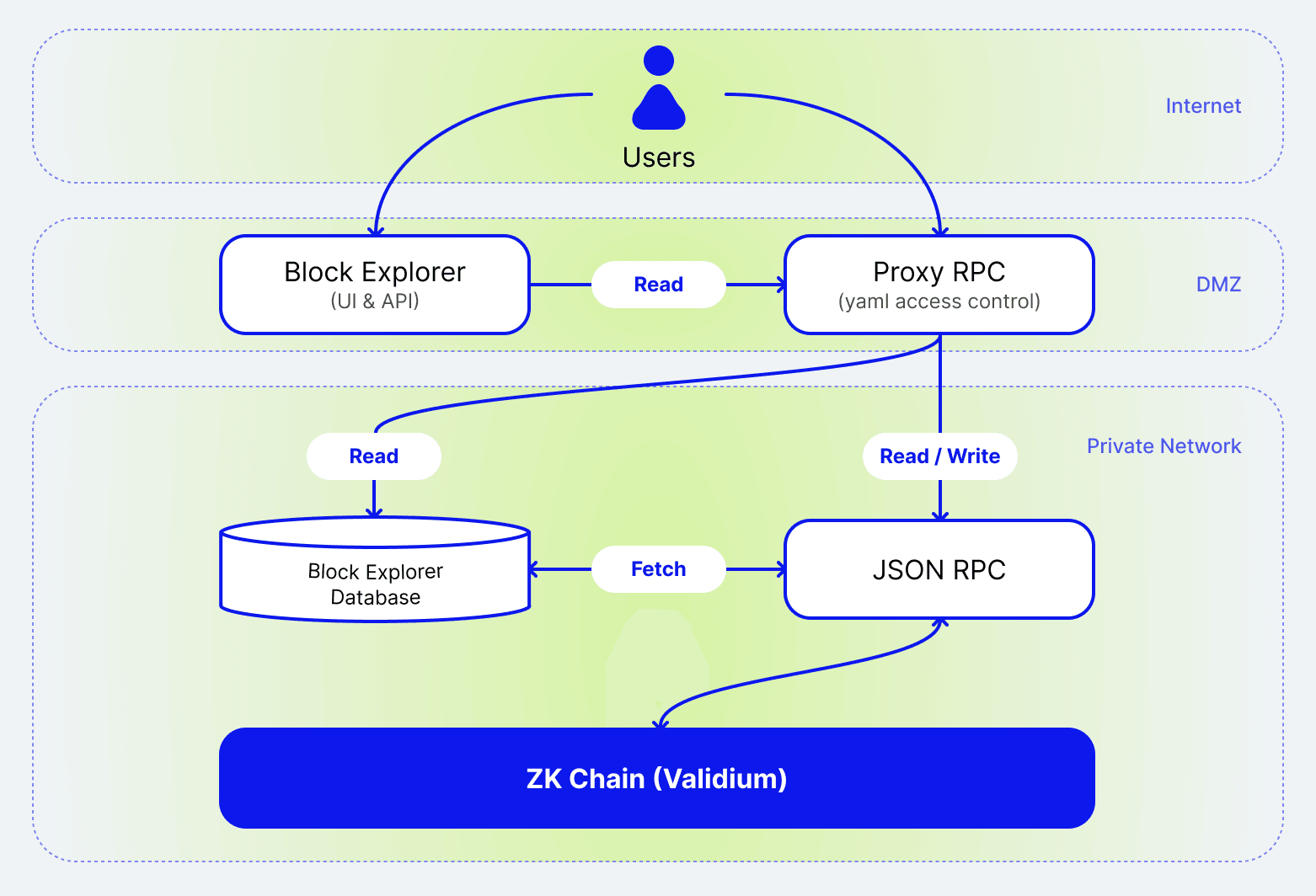
Components
Prividium™ extends the ZK Stack architecture with dedicated modules for privacy, governance, and access control. These components work together to provide secure, verifiable, and customizable network operations.
- Permissioning System: A built-in role-based framework that manages users, roles, permissions, and selective disclosure through the Admin Dashboard. Administrators define who can read or write to contracts and configure disclosure settings without modifying code or YAML files.
- Proxy RPC: The secure interface that filters every request based on the policies defined in the Permissioning System. It validates user tokens issued via Okta or crypto-native (SIWE) login and enforces role and argument-level restrictions before forwarding to the sequencer.
- Private Block Explorer: A self-hosted explorer with access restrictions aligned to user roles. It allows authorized participants to view transactions, blocks, and state data while protecting sensitive information from public exposure.
- ZKsync Chain: A private ZKsync Chain deployed within your infrastructure. It includes a dedicated sequencer and prover that execute transactions and generate zero-knowledge proofs locally.
- ZKsync Gateway: Receives zero-knowledge proofs and publishes commitments to Ethereum. This ensures data integrity, anchors the private chain to Ethereum, and enables future cross-chain interoperability.
How Access Control Works
- Users authenticate via Okta SSO or Sign-in With Ethereum (SIWE) in the User Dashboard.
- The Proxy RPC forwards their request and token to the Prividium API.
- The Prividium API verifies the user’s identity, role, and function-level rules.
- Authorized requests are sent to the Sequencer RPC, which executes transactions privately.
- State updates are committed to Ethereum through the ZKsync Gateway.
This design ensures that access control, compliance, and selective disclosure are built directly into the network stack, not managed through static configuration files.